Page All: Viewing All Pages
Page 1
Original Report 11/04/04. © Joseph Kukis & Aron Schatz.
Abstract:
The purpose of this report is to compile information on the use of wireless networks in Hoboken. It will attempt to discover where there are insecure wireless networks and to pinpoint them onto a map using standard GPS technology.
Using standard wireless tools, we will attempt to perform warchalking. The term warchalking means that we will find where wireless networks are in a given area, chalking them on a map. On the software side, Netstumbler .4 will be used from http://www.netstumbler.com and Stumbverter will be used from http://www.sonar-security.com/sv.html to convert the stumbler data to a usable format for use in Mappoint 2004, the mapping software we used to display the AP (access point) data.
On the hardware side, we used the standard Stevens issued Compaq Armada E500. It was paired with a Compaq WL110 wireless card that is a rebranded Orinoco card, which is a supported card for the Netstumbler program. For the GPS, we used a Tripmate GPS that is made from Delorme and attaches to the serial port of the laptop.
Introduction:
Wireless networking has been one of the biggest technological pushes for the industry. The news and other media are riddled with stories on wireless technology. While the technology enables people to roam free around an area, it isn’t without its fair share of problems. For instance, how can you be sure that a wireless network is safe and secure from intrusion? From a hardware point of view, it is relatively easy to secure a normal wired LAN. You know where the connections are and who is using them. Wireless is inherently different. You can’t be sure that a wireless network won’t extend beyond your sphere of influence. This is why there are some safeguards that allow wireless networks to work in today’s world.
Encryption is the best way to secure a wireless network. The problem is that many consumers and even companies forget to secure their own network. This is a major problem if they want a secure network with some safeguards from intrusion. There are networks that welcome the free access, and that is fine with respect to what they accomplish. It is the ones that people setup and have no idea how to setup. This report will go into detail on a cross section of wireless networks in Hoboken, where they are used, and how secure they actually are.
Original Report 11/04/04. © Joseph Kukis & Aron Schatz.
Abstract:
The purpose of this report is to compile information on the use of wireless networks in Hoboken. It will attempt to discover where there are insecure wireless networks and to pinpoint them onto a map using standard GPS technology.
Using standard wireless tools, we will attempt to perform warchalking. The term warchalking means that we will find where wireless networks are in a given area, chalking them on a map. On the software side, Netstumbler .4 will be used from http://www.netstumbler.com and Stumbverter will be used from http://www.sonar-security.com/sv.html to convert the stumbler data to a usable format for use in Mappoint 2004, the mapping software we used to display the AP (access point) data.
On the hardware side, we used the standard Stevens issued Compaq Armada E500. It was paired with a Compaq WL110 wireless card that is a rebranded Orinoco card, which is a supported card for the Netstumbler program. For the GPS, we used a Tripmate GPS that is made from Delorme and attaches to the serial port of the laptop.
Introduction:
Wireless networking has been one of the biggest technological pushes for the industry. The news and other media are riddled with stories on wireless technology. While the technology enables people to roam free around an area, it isn’t without its fair share of problems. For instance, how can you be sure that a wireless network is safe and secure from intrusion? From a hardware point of view, it is relatively easy to secure a normal wired LAN. You know where the connections are and who is using them. Wireless is inherently different. You can’t be sure that a wireless network won’t extend beyond your sphere of influence. This is why there are some safeguards that allow wireless networks to work in today’s world.
Encryption is the best way to secure a wireless network. The problem is that many consumers and even companies forget to secure their own network. This is a major problem if they want a secure network with some safeguards from intrusion. There are networks that welcome the free access, and that is fine with respect to what they accomplish. It is the ones that people setup and have no idea how to setup. This report will go into detail on a cross section of wireless networks in Hoboken, where they are used, and how secure they actually are.
Page 2
Wireless Technology:
Before we can start to discuss our wireless study of Hoboken, we must briefly go over the current state of wireless technology and security. Wireless networks encompass the IEEE 802.11 standard. There are three primary types of wireless networks currently on the market today. The 802.11a, 802.11b, 802.11g networks are often referred to by their suffix “a”, “b”, and “g” respectively. “A” networks are the least common networks, operating in the 5 Ghz range with a speed of 54Mbps and are still very expensive to implement. 802.11a has seen limited adoption because of the high adoption rate of 802.11b, and concerns about range: at 5 GHz, 802.11a cannot reach as far with the same power limitations, and may be absorbed more readily.
The other two more popular standards operate in the 2.4 Ghz range, with 802.11b transmitting data at a maximum speed of 11Mbps, and 802.11g transmitting data at a max speed of 54Mbps. Currently most networks are implementing a “b” variety network due to the low cost and the fact that it has been on the market the longest. “G” networks are quickly overtaking “B” technology due to increased transferred speeds, interoperability, further distance, and enhanced security options. In the near future 802.11n will be making an appearance and offer even higher transfer speeds of around 100Mbps which approaches the speeds of current wired networks.
Wireless Security:
Due to the inherent nature of wireless, they are far less secure than there wired counterparts. The reason for this can be traced to the popularity of wireless. Wireless networking is now firmly entrenched in the home computer market, and that means that the people buying the products cannot be assumed to have any form of expertise in technology, meaning the products had better be extremely easy to set up, and use. This creates a huge problem because when a manufacturer provides ease of use, it usually means that the security will suffer. More complex systems are usually much more secure than easy to use systems. Take Windows and Linux for example, Windows may be easy to use, but Linux is more secure. This is true throughout the industry. Even with WEP and WPA security, it is more of a deterrent than a block. The persistent cracker can gain access to these wireless networks.
The 802.11 specification included WEP (Wired Equivalent Privacy) in the beginning of the standard. WEP comes primarily in two forms; 64-bit and 128-bit encryption. The data packets are encrypted from the access point using the non-rotating key. WEP provides only access point verification for the client. Unlike WPA (Wi-Fi Protected Access), it does not provide client authentication. There are free tools available that allow you to capture wireless packets and to break the encryption key for WEP.
802.11i is the newest standard for wireless security, WPA is one benefit of it. WPA provides a much better security model for wireless networks. Not only does it provide client authentication (not the other way around), it blocks transmission for an unauthorized client until they are authorized. WPA provides greatly enhanced security on a per packet basis, and if combined with network security policies such as MAC address filtering can provide a greatly enhanced secure network.
The biggest problem facing the security of networks is the default setting when a product is setup. Consumers usually don’t bother to setup a device if it works correctly out of the box. This leads to most consumers having very insecure wireless networks and any random person can connect and use their resources, even crack into other computers on their network.
Study Overview:
For our study of wireless networks in Hoboken, we examined an area with a size of 4 blocks by 13 blocks in size by driving in a car equipped with a laptop using NetStumbler and a GPS unit to track the location of access points. While driving through Hoboken, Netstumbler would play a sound whenever it detected a new wireless network and has the ability to detect such information as GPS Coordinates, network type, MAC address, SSID, Encryption State, vendor, channel, and signal strength in real time. After collecting the data we brought it back to a computer running Stumbverter which takes the GPS coordinates and plots them on a map showing the location of every access point detected. In the next section we will discuss the results of our study.
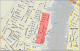
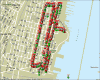
Area of Study –Hoboken, NJ
Results:
Our study produced an excellent sample of wireless networks in Hoboken, NJ. We were able to detect 818 wireless networks in the area of study, 810 of which were actual access points. Of the 818 networks detected, 63.33% were 802.11b networks and 36.67% were 802.11g networks. When looking at the security portion of the study we discovered that 57.33% of the wireless networks didn’t have any encryption enabled, and 26.77% of wireless networks contained the default SSID. Both of these results will be discussed in detail below. The study also showed us which vendors the majority of wireless users used for their networks with the top three vendors being Linksys, Netgear, and D-Link(See Table Below).
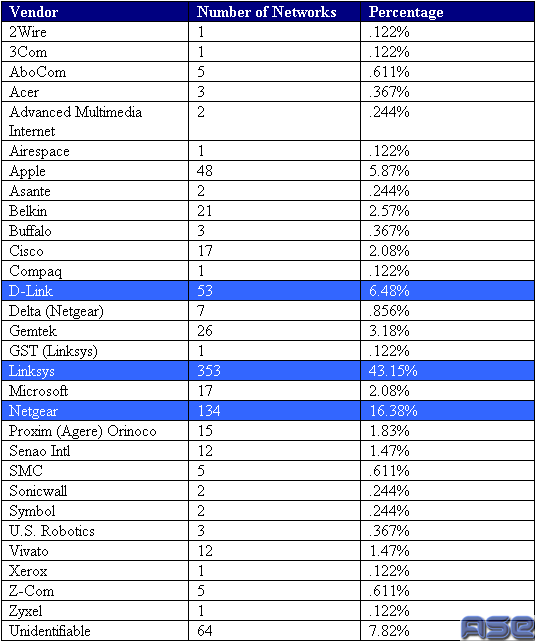
Top 3 Wireless Vendors: Linksys (43.15%) , Netgear (16.38%), D-Link (6.48%)
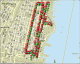
Map showing Wireless Access Points in Hoboken (Green=Encrypted, Red=UnEncrypted)
Wireless Technology:
Before we can start to discuss our wireless study of Hoboken, we must briefly go over the current state of wireless technology and security. Wireless networks encompass the IEEE 802.11 standard. There are three primary types of wireless networks currently on the market today. The 802.11a, 802.11b, 802.11g networks are often referred to by their suffix “a”, “b”, and “g” respectively. “A” networks are the least common networks, operating in the 5 Ghz range with a speed of 54Mbps and are still very expensive to implement. 802.11a has seen limited adoption because of the high adoption rate of 802.11b, and concerns about range: at 5 GHz, 802.11a cannot reach as far with the same power limitations, and may be absorbed more readily.
The other two more popular standards operate in the 2.4 Ghz range, with 802.11b transmitting data at a maximum speed of 11Mbps, and 802.11g transmitting data at a max speed of 54Mbps. Currently most networks are implementing a “b” variety network due to the low cost and the fact that it has been on the market the longest. “G” networks are quickly overtaking “B” technology due to increased transferred speeds, interoperability, further distance, and enhanced security options. In the near future 802.11n will be making an appearance and offer even higher transfer speeds of around 100Mbps which approaches the speeds of current wired networks.
Wireless Security:
Due to the inherent nature of wireless, they are far less secure than there wired counterparts. The reason for this can be traced to the popularity of wireless. Wireless networking is now firmly entrenched in the home computer market, and that means that the people buying the products cannot be assumed to have any form of expertise in technology, meaning the products had better be extremely easy to set up, and use. This creates a huge problem because when a manufacturer provides ease of use, it usually means that the security will suffer. More complex systems are usually much more secure than easy to use systems. Take Windows and Linux for example, Windows may be easy to use, but Linux is more secure. This is true throughout the industry. Even with WEP and WPA security, it is more of a deterrent than a block. The persistent cracker can gain access to these wireless networks.
The 802.11 specification included WEP (Wired Equivalent Privacy) in the beginning of the standard. WEP comes primarily in two forms; 64-bit and 128-bit encryption. The data packets are encrypted from the access point using the non-rotating key. WEP provides only access point verification for the client. Unlike WPA (Wi-Fi Protected Access), it does not provide client authentication. There are free tools available that allow you to capture wireless packets and to break the encryption key for WEP.
802.11i is the newest standard for wireless security, WPA is one benefit of it. WPA provides a much better security model for wireless networks. Not only does it provide client authentication (not the other way around), it blocks transmission for an unauthorized client until they are authorized. WPA provides greatly enhanced security on a per packet basis, and if combined with network security policies such as MAC address filtering can provide a greatly enhanced secure network.
The biggest problem facing the security of networks is the default setting when a product is setup. Consumers usually don’t bother to setup a device if it works correctly out of the box. This leads to most consumers having very insecure wireless networks and any random person can connect and use their resources, even crack into other computers on their network.
Study Overview:
For our study of wireless networks in Hoboken, we examined an area with a size of 4 blocks by 13 blocks in size by driving in a car equipped with a laptop using NetStumbler and a GPS unit to track the location of access points. While driving through Hoboken, Netstumbler would play a sound whenever it detected a new wireless network and has the ability to detect such information as GPS Coordinates, network type, MAC address, SSID, Encryption State, vendor, channel, and signal strength in real time. After collecting the data we brought it back to a computer running Stumbverter which takes the GPS coordinates and plots them on a map showing the location of every access point detected. In the next section we will discuss the results of our study.

Area of Study –Hoboken, NJ
Results:
Our study produced an excellent sample of wireless networks in Hoboken, NJ. We were able to detect 818 wireless networks in the area of study, 810 of which were actual access points. Of the 818 networks detected, 63.33% were 802.11b networks and 36.67% were 802.11g networks. When looking at the security portion of the study we discovered that 57.33% of the wireless networks didn’t have any encryption enabled, and 26.77% of wireless networks contained the default SSID. Both of these results will be discussed in detail below. The study also showed us which vendors the majority of wireless users used for their networks with the top three vendors being Linksys, Netgear, and D-Link(See Table Below).

Top 3 Wireless Vendors: Linksys (43.15%) , Netgear (16.38%), D-Link (6.48%)

Map showing Wireless Access Points in Hoboken (Green=Encrypted, Red=UnEncrypted)
Page 3
Analysis:
Looking at the results, one can come to the decision that there has been an explosion in wireless network growth in the past 3 to 4 years. With over 800 networks detected in such a small area like Hoboken, it is a good indication that consumers are looking towards wireless technology as an easy way to network their houses.
Another statistic to look at is the number of 802.11b vs. 802.11g networks that were discovered. Our results show that 63.33% of users were using 802.11b networking technology to network their houses and 36.67% were using 802.11g technology. This can be attributed to the fact that 802.11b technology came out first, and that it costs less money to implement then 802.11g. As 802.11b technology gets replaced by the newer 802.11g and 802.11n, the number of users using 802.11b will probably decrease.
By looking at our results of the vendors of the wireless equipment being used in Hoboken we came to the conclusion that Linksys, Netgear, and D-Link are the top three brands. This is not surprising since Linksys was one of the first manufacturers to roll out a consumer wireless product, with Netgear and D-link following closely behind.
Perhaps the most important part of the study is the results that deal with security. Our results show that 57.33% of wireless networks had no encryption enabled at all, and 26.77% of wireless networks were still using the default SSID. As discussed in the Wireless security section, wireless networks are inherently insecure because they transmit data through the air. The number of users without wireless encryption produces a very large problem indicating that wireless encryption is either a) too hard to set up for the average user or b) the importance of encryption is not made clear to end users. By taking as little as 10-15 minutes of your time to set up encryption you would be able to deter any people trying to steal internet access or break into your network. The issue of 26.77% of wireless networks using the default SSID, indicates that most of the users probably installed the wireless access point without changing any settings which include encryption, SSID, and default login/passwords. Again, this indicates that manufacturers need to stress the importance of taking the time to change default settings on a wireless router and enable security.
Conclusion:
Overall our results seem to be a good sample set of wireless networks and their users from Hoboken, NJ. The results show what we expected to happen with a good sized amount of users not enabling encryption or changing any settings at all. The study shows that manufacturers need to do their part to emphasize the importance of wireless security, and not market their products as a “quick and easy way” to set up a network. Users also should be more educated when they go shopping and look to sources such as the internet or magazines for information on wireless technology and what precautions to take. Some simple suggestions we make to users are to enable encryption on their router whether it is WEP or WPA, change the SSID or disable SSID broadcast to make it more difficult for war drivers to detect your network, enable MAC filtering, and disable DHCP and use static IP addresses. All of these methods have ways they can be defeated but they all act as deterrents to people looking to hack into your network or steal internet access. Wireless networking will definitely be around for awhile due to its many advantages; however users should be advised before setting up their networks so they can surf both easily and securely.
Analysis:
Looking at the results, one can come to the decision that there has been an explosion in wireless network growth in the past 3 to 4 years. With over 800 networks detected in such a small area like Hoboken, it is a good indication that consumers are looking towards wireless technology as an easy way to network their houses.
Another statistic to look at is the number of 802.11b vs. 802.11g networks that were discovered. Our results show that 63.33% of users were using 802.11b networking technology to network their houses and 36.67% were using 802.11g technology. This can be attributed to the fact that 802.11b technology came out first, and that it costs less money to implement then 802.11g. As 802.11b technology gets replaced by the newer 802.11g and 802.11n, the number of users using 802.11b will probably decrease.
By looking at our results of the vendors of the wireless equipment being used in Hoboken we came to the conclusion that Linksys, Netgear, and D-Link are the top three brands. This is not surprising since Linksys was one of the first manufacturers to roll out a consumer wireless product, with Netgear and D-link following closely behind.
Perhaps the most important part of the study is the results that deal with security. Our results show that 57.33% of wireless networks had no encryption enabled at all, and 26.77% of wireless networks were still using the default SSID. As discussed in the Wireless security section, wireless networks are inherently insecure because they transmit data through the air. The number of users without wireless encryption produces a very large problem indicating that wireless encryption is either a) too hard to set up for the average user or b) the importance of encryption is not made clear to end users. By taking as little as 10-15 minutes of your time to set up encryption you would be able to deter any people trying to steal internet access or break into your network. The issue of 26.77% of wireless networks using the default SSID, indicates that most of the users probably installed the wireless access point without changing any settings which include encryption, SSID, and default login/passwords. Again, this indicates that manufacturers need to stress the importance of taking the time to change default settings on a wireless router and enable security.
Conclusion:
Overall our results seem to be a good sample set of wireless networks and their users from Hoboken, NJ. The results show what we expected to happen with a good sized amount of users not enabling encryption or changing any settings at all. The study shows that manufacturers need to do their part to emphasize the importance of wireless security, and not market their products as a “quick and easy way” to set up a network. Users also should be more educated when they go shopping and look to sources such as the internet or magazines for information on wireless technology and what precautions to take. Some simple suggestions we make to users are to enable encryption on their router whether it is WEP or WPA, change the SSID or disable SSID broadcast to make it more difficult for war drivers to detect your network, enable MAC filtering, and disable DHCP and use static IP addresses. All of these methods have ways they can be defeated but they all act as deterrents to people looking to hack into your network or steal internet access. Wireless networking will definitely be around for awhile due to its many advantages; however users should be advised before setting up their networks so they can surf both easily and securely.